Financial Services
Secret Computing® is being used in production at some of the largest, multinational financial services firms today. Read up on one of the four major uses cases driving value for our customers:
Fraud Data Collaboration
The One Sentence Summary: Financial institutions are able to improve the predictiveness of their fraud detection models by privately computing on fraud data from partner banks.

Customer Case Study
FRAUD DATA COLLABORATION
Industry: Financial Services
Application Area: Fraud & Risk Models
Functions: Private Intersection, Logistic Regression
Situation: A large multinational financial services firm wants to improve their fraud detection and risk models by accessing more data. Fraud is always an issue for financial institutions, but the COVID-19 crisis has fueled a rise in fraud and financial crimes, which has accelerated innovation in fraud detection at-large.
Complication: Fraud data sharing initiatives have historically been difficult for the firm to implement for several reasons, including jurisdictional restrictions, data confidentiality concerns, and trade secret sensitivities.
Resolution: XOR enables the financial services firm to train their fraud and risk models on distributed data from participating partner banks while maintaining all parties’ security and privacy requirements. In the chart below, Model 1 includes data from only one bank; Model 2 from two banks; and Model 3 from three banks.
Outcomes:
-
Improved predictive accuracy, specifically in identifying outliers and fraudulent transactions
-
Additional sample size continues to add predictive insights
-
Additional bad samples allows for more robust models
-
Increased model performance reduces volume and time in manual review process
-
Identify more financial criminals
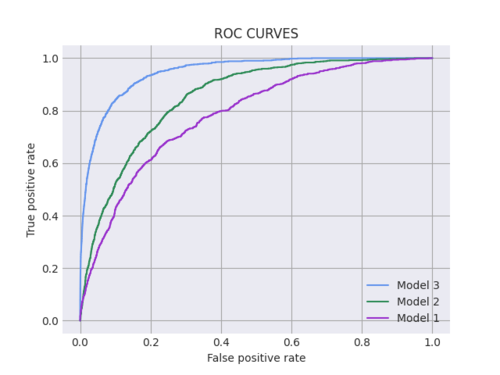
More Bank Data = Better Models
Model 1 includes data from only one bank
Model 2 includes data from two banks
Model 3 includes data from three banks
CURIOUS TO LEARN MORE ABOUT FRAUD DATA COLLABORATION?
HERE’S A DEEPER DIVE
Regulators are increasingly interested and actively exploring how financial institutions can engage in secure, private data-sharing to fight financial crime. For example, in August 2019, Inpher took part in the Financial Conduct Authority (FCA) 2019 Global AML and Financial Crime TechSprint held in London. The purpose of the TechSprint was to determine how privacy-enhancing technologies (PETs) can effectively combat financial crime, detect fraudulent activities, and prevent money laundering within the financial services industry. Inpher was invited by the FCA to apply its expertise in PETs (specifically, secure multiparty computation) to problems in fraud detection and anti-money laundering (AML). Inpher also won the People’s Choice Award for best solution at the end of the TechSprint. Please do check out our blogpost on the TechSprint for an overview of the problem and our solution as well as our CTO Dr. Dimitar Jetchev’s presentation at Real World Cryptographic 2019.
Privacy-enhancing technologies are garnering growing attention in the media, and organizations are adopting them more than ever before. Although organizations are leveraging Secret Computing® today for fraud data collaborations, there are many other exciting areas in which secure, private data-sharing will be transformative for the bank and others. Examples include applications in – anti-money laundering (AML) applications (Detecting Money Laundering Activities via Secure Multi-Party Computation Network Flow Analysis), know-your-customer (KYC) protocols, portfolio analytics, regulatory reporting, trade flows and execution, and more.
LET’S TALK!
Please contact our Business Development and Solutions team to learn more about Fraud Data Collaboration!
Double-Blind Trade Matching
The One Sentence Summary: Financial institutions are able to effectively find trading partners in over-the-counter (OTC) markets through private matching in which no unnecessary trade positions are leaked to the broader market.
Customer Case Study
DOUBLE-BLIND TRADE MATCHING
Industry: Financial Services
Application Area: Capital Markets & Trading
Functions: Private Set Intersection & Oblivious Compare
Situation: A large multinational financial services firm and their buy-side clients reveal sensitive trading positions in OTC markets, even in dark pools.
Complication: Leaked positions have adverse consequences for buy and sell-side, including unfavorable pricing, reduced liquidity, and general market inefficiencies.
Resolution: XOR enables the financial institution and their clients to find trading partners in OTC markets without unnecessarily revealing sensitive positions.
Outcomes:
-
Improved liquidity in OTC markets
-
More favorable asset pricing
-
No position leakage; cryptographically secure
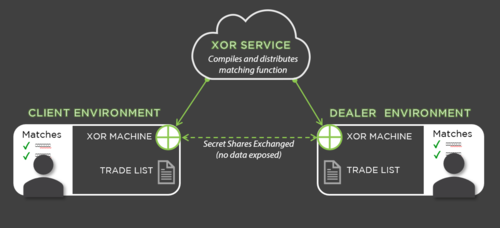
A Simple Trade Matching Set-Up
Trade matching also works for an ecosystem of traders (3+) though only two are shown here.
CURIOUS TO LEARN MORE ABOUT DOUBLE-BLIND TRADE MATCHING?
HERE’S A DEEPER DIVE
Information is valuable in the capital markets and the leaking of information about a participant’s intentions can lead to disadvantageous pricing, the reverse engineering of trading strategies, or worse. This is especially so in the expansive OTC markets where large dealers and institutional clients can assemble and trade significant positions on oftentimes complex and illiquid securities.
The ability to blindly match offsetting trading positions among one or more parties is now available using Inpher’s XOR Secret Computing Engine. This process improves efficiency, liquidity, and volume in the given market. The participants are only informed when there is a match and can then negotiate or automate pricing. No individual party or third party is exposed to the list of positions or instruments ensuring that there is no information leakage. Leading dealers and their institutional clients are currently using the XOR Engine solution for trading in production.
How It Works
-
Daily, each participating trader submits their axe list of positions they are looking to buy and sell onto their XOR virtual machine. This list never leaves their privacy zone and is not exposed to any other party.
-
The trader submits an instruction to the Inpher XOR Engine to attempt to find a match between the two or more axe lists.
-
The XOR Service complies and distributes the secret matching function to the XOR Machines within each respective trader’s privacy zones.
-
The XOR Machines execute the circuit and communicate with each other to exchange secret shares and then compute with random numbers.
-
If there is a partial or full match on a trade between the parties, each side receives only the aggregate number of matches and the sum of the notional value.
-
Each trader decides if they want to reveal the matched position.
-
If they decide to reveal, a second submission to the XOR Engine is run and each trader receives the revealed output of the individual matched trading positions for the price negotiation and execution.
CURIOUS TO LEARN MORE ABOUT DOUBLE-BLIND TRADE MATCHING?
LET’S TALK!
Please contact our Business Development and Solutions team to learn more about Double-Blind Trade Matching!
Consumer Credit Modeling
The One Sentence Summary: Financial institutions are able to improve the predictiveness of its consumer credit models by privately computing on restricted internal data assets and external partner data.

Customer Case Study
CONSUMER CREDIT MODELING
Industry: Financial Services
Application Area: Consumer Credit Models
Functions: Logistic Regression
Situation: A large multinational financial institution wants to improve its consumer credit models by accessing more data.
Complication: Sensitive data assets are restricted across partners, business units, and jurisdictions.
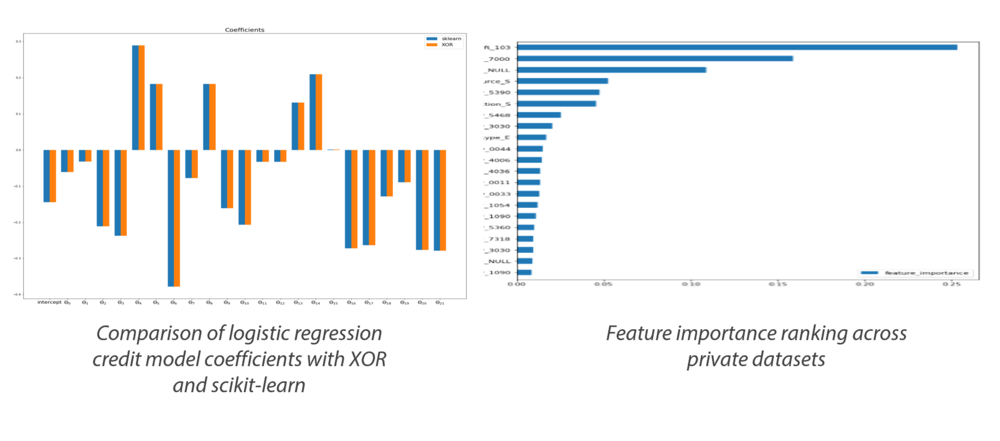
Resolution: XOR enables the firm to compute across private datasets in order to train more accurate models using the combined feature set. XOR also enables the client and partners to privately execute inference on the private production model and private data for evaluation and scoring.
Outcomes:
-
XOR maintains precision of up to 9 digits (0.000000001) to ensure regulatory compliance with existing reported credit models
-
Predictive features can be identified and joined across distributed, private datasets without moving or revealing the underlying sensitive data
CURIOUS TO LEARN MORE ABOUT CONSUMER CREDIT MODELING?
LET’S TALK!
Please contact our Business Development and Solutions team to learn more about Consumer Credit Modeling!
Uncleared Margin Rules (UMR)
The One Sentence Summary: Financial institutions are able to privately compute on institutional client assets visible to them, as well as assets the client holds away from the bank to calculate initial margin more efficiently.

Customer Case Study
UNCLEARED MARGIN RULES
Industry: Financial Services
Application Area: Regulatory/Market Risk
Functions: Private Set Intersection & Statistical Analysis
Situation: Institutional clients want to have their initial margins calculated in real-time and optimize their collateral.
Complication: The existing process contributes to over-collateralizing positions, increasing drag on portfolio performance. It also involves a time delay and releasing aspects of sensitive trading position data.
Resolution: XOR enables banks to privately compute on institutional client assets visible to them, as well as assets the client holds away from the bank to calculate initial margin more efficiently.
Outcomes:
-
Institutional client protects their sensitive, individual security position data
-
Optimizes the collateral requirements
-
Cutting down on drag
-
Regulators are satisfied that margin requirements are being met
-
Bank adds value by freeing up capital for the institutional client and potentially driving more trading revenue
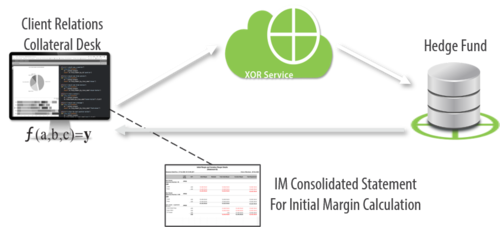
A Simple UMR Set-Up
(Illustrative)
CURIOUS TO LEARN MORE ABOUT UNCLEARED MARGIN RULES?
LET’S TALK!
Please contact our Business Development and Solutions team to learn more about Uncleared Margin Rules!

